Philippe Vannier Executive Vice President Big Data & Security Solutions and Group CTO, Atos wrote a very interesting piece on key 2020+ technologies set to impact manufacturers in the coming years:
He summarized the technologies in this intuitive graph:
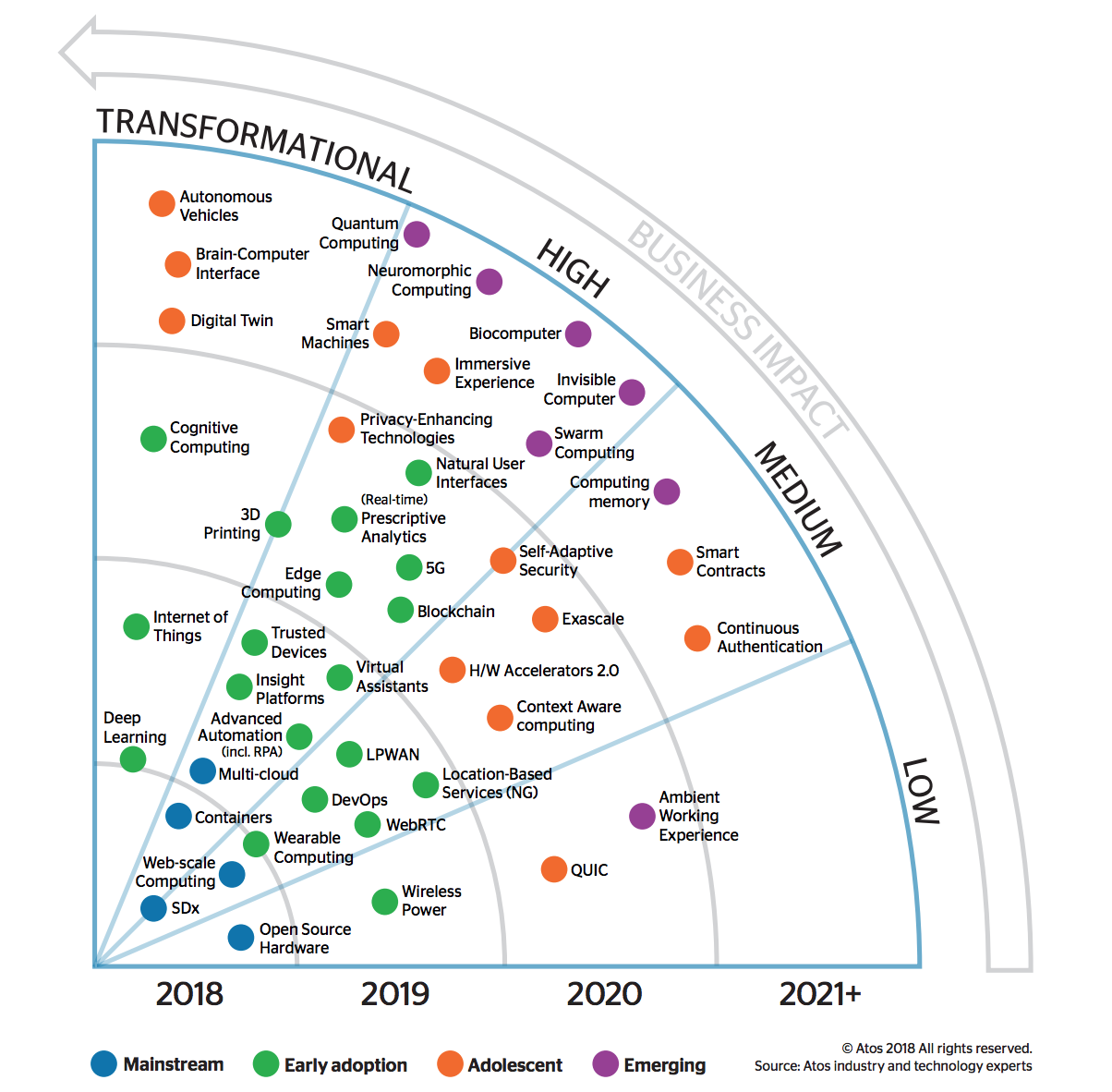
He also briefly described each of the following trends we briefly summarized below:
- 3D Printing - the inexpensive approach to manufacturing 3D objects, materializing them from virtual designs created using CAD (Computer Added Aided Design) programs.
- 5G - the next generation of communication networks and services.
- Ambient Working Experience - free flow across devices and the portability of the user persona across multiple create and consume device types.
- Autonomous Vehicles - the interaction of transportation vehicles and robotic capabilities, such as environmental sensors, context awareness and autonomous decision-making using Artificial Intelligence.
- Biocomputer - computers that use biological materials such as DNA and proteins to perform computational calculations that involve the storage, retrieving and processing of data.
- Blockchain - a distributed database that uses cryptographic techniques to store a growing list of records – or blocks – sequentially.
- Brain-Computer Interface - direct communication pathway between the brain and an external device based on neural activity generated by the brain.
- Cognitive Computing - integration of algorithms and methods from diverse fields such as Artificial Intelligence (AI), machine learning, Natural Language Processing (NLP) and knowledge representation to enhance human performance on cognitive tasks.
- Computing memory - represents a new approach to solving the limitations of classical (Von Neumann) computing architectures. In this model, certain computational tasks are performed in place in a specialized memory unit called computational memory.
- Containers - provide users and applications running inside them with the illusion and experience of running on their own dedicated machine.
- Context-Aware Computing - systems collect and store diverse data, then leverage analytics to deduce context from the interactions among the data before triggering actions based on that contextual information.
- Continuous Authentication - exploits behavioral (passive) biometrics (a form of biometrics that exploits dynamic human characteristics) to establish that an individual is who they say they are ( voice, typing style, mouse use and walking pace).
- Deep Learning - a branch of machine learning with its roots in neural networks where multi-layered neural network algorithms attempt to model high-level abstractions in data.
- DevOps - a philosophy for how to build and operate software that encourages teams to focus on business value, work collaboratively, deploy software more frequently in smaller increments and build reliable solutions.
- Digital Twin - a digital replica of a physical asset, process, system or service across its lifecycle
- Edge Computing - moves applications, data and services away from the centralized model of Cloud computing to a more decentralized model that lies at the extremes of the network.
- Exascale - HighPerformance Computing (HPC) systems capable of at least one billion billion calculations per second (one exaFLOPS) — a thousand-fold increase over today’s petascale supercomputers
- H/W Accelerators 2.0 - highly specialized computing devices targeting a narrow field of computing. They can be classified roughly into three categories: programmable hardware (like GPUs), Field Programmable Gate Arrays (FPGA) and fixed-function hardware (like Google Tensor Processing Unit).
- Immersive Experience - encompass a wide range of devices,including virtual reality (VR) – digital simulations of real-world environments; 3D displays – display devices that create the perception of depth; haptic devices – which add the sensation of touch; and holographic user interfaces – laser-based volumetric displays where users interact with holographic images.
- Insight Platforms - the third generation of business analytics platforms, after the Business Intelligence and Big Data phases
- Intelligent Automation - Robotic Process Automation (RPA) or knowledgebased and/or AI-supported automation solutions that are transforming the existing automation solutions.
- Internet of Things - ubiquitous communication networks that effectively captures, manages and leverages data from billions of real-life objects and physical activities.
- Invisible Computer - the rise of technologies like speech recognition, chatbots, XR (AR/VR/ MR) and advanced machine learning, devices that deeply and naturally integrate into our everyday lives.
- Location- Based Services - Geographical information systems (GIS) capture, store, analyze and display information referenced according to its geographical location.
- LPWAN - LowPower Wide-Area Network (LPWAN) wireless communication technology has a low power requirement and a long range, but a low data rate.
- Multi-Cloud - models with diverse, decentralized and autonomic management and hybrid Cloud models that cross boundaries between internal and external Cloud services or between public, private and community providers
- Natural User Interfaces - systems designed to make human-computer interaction feel as natural as possible.
- Neuromorphic Computing - systems integrate electronic analog circuits with digital ones to mimic neuro-biological architectures similar to those of nervous systems of living beings.
- Open Source Hardware - extends the ideas and methodologies popularized in open source software development to hardware development.
- Privacy-Enhancing Technologies - technologies involved in protecting or masking personal data (whether employees, customers or citizens) to achieve compliance with data protection legislation and sustain customers’ trusted relationships
- Quantum Computing - uses quantum-mechanical phenomena to execute operations on data
- QUIC - provides multiplexing and flow control equivalent to HTTP/2; security
- Real-time Prescriptive Analytics - advanced form of business analytics that helps decision-makers determine the best course of action among various choices, given known parameters.
- SDx - Software-defined anything/everything (SDx) is an approach that replaces legacy with software running on commodity hardware platforms.
- Self-Adaptive Security - relies on new generations of context-aware security technologies that dynamically adapt to threats.
- Smart Contracts - digital peer-to-peer contracts written into lines of programming code.
- Smart Machines - systems embedded with cognitive computing capabilities that are able to make decisions and solve problems without human intervention
- Swarm Computing - combines network and Cloud capabilities to create on-demand, autonomic and decentralized computing.
- Trusted Devices - rely on highsecurity design, hardened software and hardware, and intensive certification processes provided by trusted third parties.
- Virtual Assistants - software agents that perform services or tasks on our behalf.
- Wearable Computing - bracelets, headbands and helmets, contact glasses, earphones, globes, digital pens, smart clothing, jewelry and even tattoos.
- WebRTC - open standard for Web Browser based Real-Time Communications and is supported by all major browser vendors, including Google Chrome, Mozilla Firefox, Microsoft Edge and Apple Safari.
- Web-scale Computing - a large, distributed, grid computing environment that can scale-out efficiently as data volumes and workload demands increase in internet-size ways.
- Wireless Power - transmission of electrical power without solid wires, using electromagnetic fields instead.
SOURCE: https://atos.net/content/mini-sites/look-out-2020/assets/pdf/ATOS_LOOK%20OUT_TECH%20TRENDS.pdf